Security vs. User experience in the age of automated identity verifications
Kenyans are increasingly conducting transactions digitally. In January 2024, for instance, the value of mobile money transactions in Kenya stood at 7.95 trillion shillings and in January 2024, the country had 76.76 million registered mobile money accounts. Kenya also has one of the most vibrant e-commerce ecosystems in Africa, thanks to factors such as efficient online payment solutions and a high mobile Internet penetration rate. However, online fraud in the country has also been on the rise. For instance, about 10.3% of e-commerce transactions conducted during the 2023 Black Friday shopping period between 23rd and 27th November were suspected to be fraudulent. One of the approaches that promises to address this issue by verifying a user’s identity is automated identity verification (IDV).
IDV utilizes technology to electronically confirm a user’s identity against government-issued documents, databases, and biometrics. Consider the process of opening a new bank account today. Gone are the days of visiting a physical branch; instead, a bank with IDV would require you to download the required documents, fill them out, and upload the documents together with a copy of your national ID and a selfie. On the backend, the bank will utilize IDV to verify your details against a database such as the Integrated Population Registration System (IPRS) and check whether your photo is authentic and truly matches your ID photo.
The advantages of this new workflow are apparent. For example, it frees your customers from having to physically visit your premises to conduct a transaction, it is less error-prone and is cost-effective. However, IDV solutions can also be cumbersome and cause unnecessary friction when implemented as a means of fraud prevention and security instead of as a core component of the user journey. This friction can manifest in various ways, from requiring users to upload numerous documents to lengthy verification processes that interrupt the user flow. The bottom line: An IDV process that does not fit each user and their situation risks creating a poor user experience, resulting in abandoned transactions.
User experience principles
What do we mean by “poor user experience?” To answer this question, we first look at what denotes “good” user experience from the point of view of Dieter Rams, an acclaimed industrial designer who outlined 10 principles of good design. According to Dieter Rams, good design:
- Is innovative;
- Makes a product useful;
- Is aesthetic;
- Makes a product understandable;
- Is unobtrusive;
- Is honest;
- Is long-lasting;
- Is thorough down to the last detail;
- Is environmentally friendly; and
- Involves as little design as possible.
These principles, while originally intended for physical products, are equally applicable in the IDV realm. A key principle is “good design makes a product useful,’ which translates to creating a frictionless experience that seamlessly integrates into the user journey. Similarly, “good design is honest” means IDV solutions should be transparent and avoid unnecessary complexity.
Security vs. User experience: An imbalanced match?
The process of authenticating one’s users and, thus, fighting fraud and ensuring regulatory compliance is fraught with challenges, chief among them being the inherent trade-off between security measures and user experience. The more stringent the IDV measures implemented, the greater the potential impact on user experience. When companies focus solely on making their IDV process as difficult as possible to handle fraud or satisfy compliance requirements, they also risk not having any customers to verify.
The security vs. User experience imbalance is often also the case where IDV is treated as a rigid monolithic process done at the user onboarding stage which disregards customer expectations, use cases, and risk levels. For instance, verifying a user’s identity for an online gaming platform requires different steps than opening an investment account with a bank. Static, one-size-fits-all IDV flows undermine both security and experience - asking for too little information risks fraud exposure while requesting excessive data causes frustrations and drop-offs.
Narrowing the gap: Finding a balance between security and customer experience
The field of user experience lives by the mantra of personalizing and customizing the user journey, and IDV can gain by borrowing from this playbook. Identity is deeply personal, and organizations should recognize the nuances involved in verifying it effectively. Security needs, customer expectations, and regulations can vary depending on the specific use case. For instance, onboarding with an e-commerce site might require basic user information, whereas making a high-priced purchase may demand more information.
The key is to implement IDV carefully and make sure it seamlessly meshes into the user journey experience. Some of the approaches that mature IDV flows can use to harmonize security and user experience are:
- Assessing risk intelligently based on the use case, transaction value, customer history, GeoLocation data, and other signals. Higher-risk scenarios merit advanced identity proofing as compared to lower-risk ones.
- Parsing the IDV process into secure, seamless stages aligned with a particular customer’s journey and use case. For instance, just capturing the ID number may suffice when a customer is opening a support ticket while funding a securities trading account necessitates robust documentary verification.
- Dynamically upgrading verification requirements in response to failed checks, higher transaction risks, or regulations. This way, you do not expose all customers to stringent IDV.
In the end, the most important factor to consider is that any instance of IDV — whether it's during onboarding or right before a major purchase — ensures a seamless, painless interaction with your brand.
The Falu Identity approach
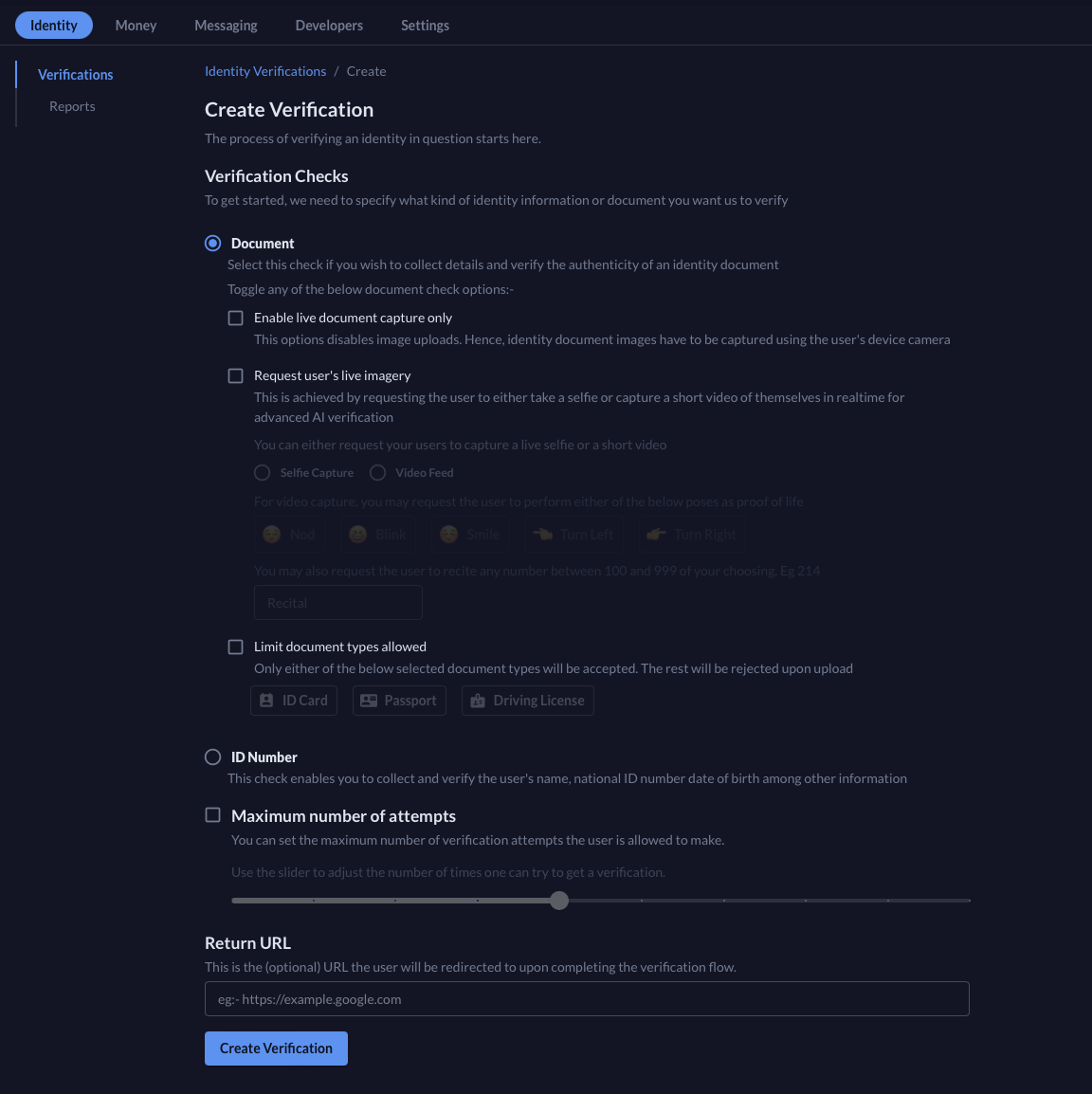
Falu Identity is built with flexibility at its core. First, we implement four methods of identity verification: database, document-based, no-document, and biometric verification. When creating an identity verification session, you can select which method, or a combination of methods, to best match your use case, security needs, and user expectations. You can also set the number of retries to a verification attempt to accommodate failed verifications that the user can correct.
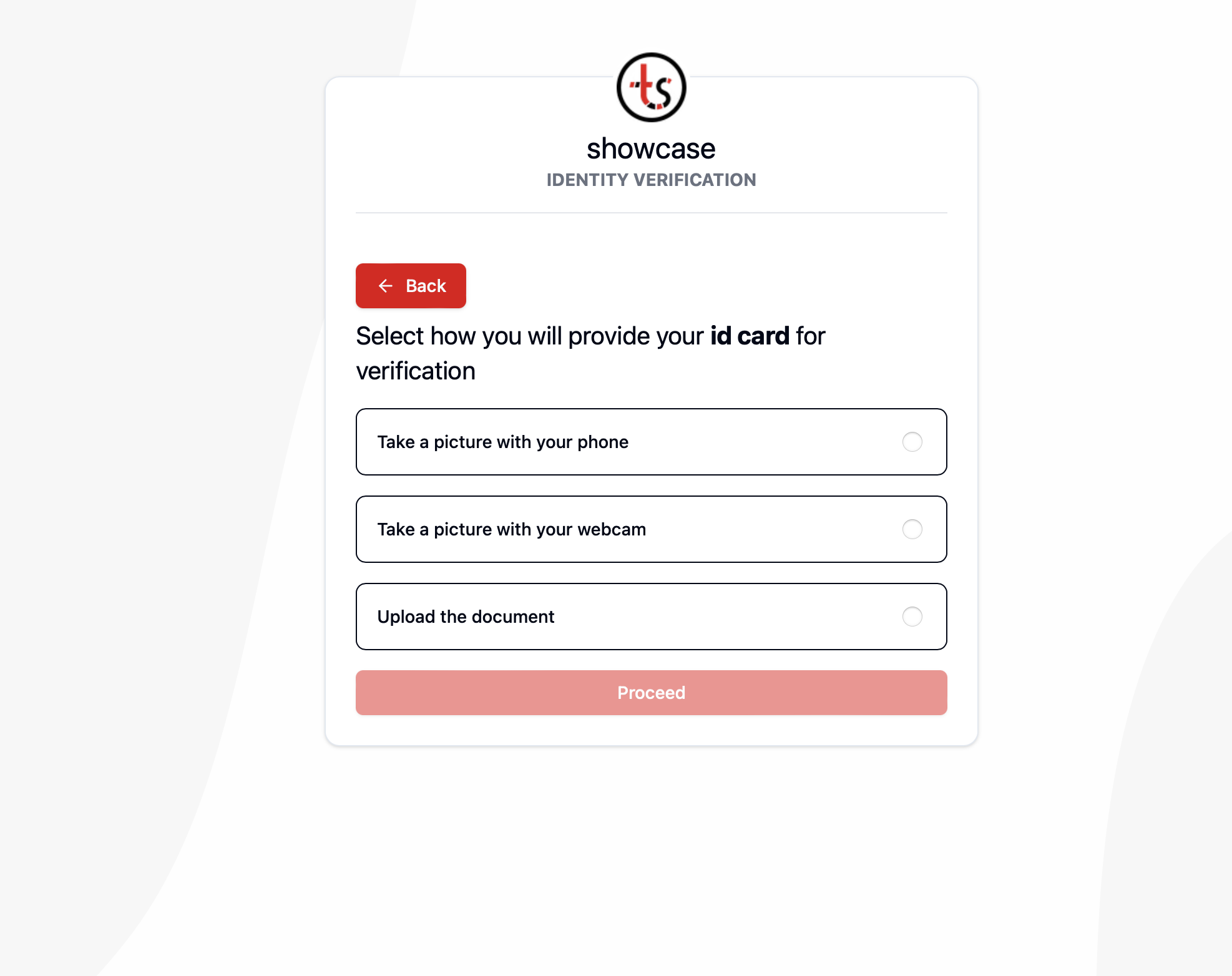
On the user end, we provide options for the user to select how best to proceed with the verification. For instance, assuming one is required to upload a copy of their ID card, Falu prompts them to either take a picture with their phone or webcam or to upload the document. Doing so allows every user to complete a verification using the approach with which they are most comfortable.
Bottom line
The key to a successful IDV strategy lies in ensuring a seamless verification flow for users. As businesses seek to address the ever-rising cases of fraud, it is our strong belief at Falu that they should tailor their IDV processes to the context of each customer. Based on this understanding, you should then work with an IDV provider who understands that no two customers are the same and, as such, provides a solution that is flexible and can meet users where they are in their journey.
Talk to us today to explore how Falu Identity can help you reach a balance between security and satisfactory user experience.